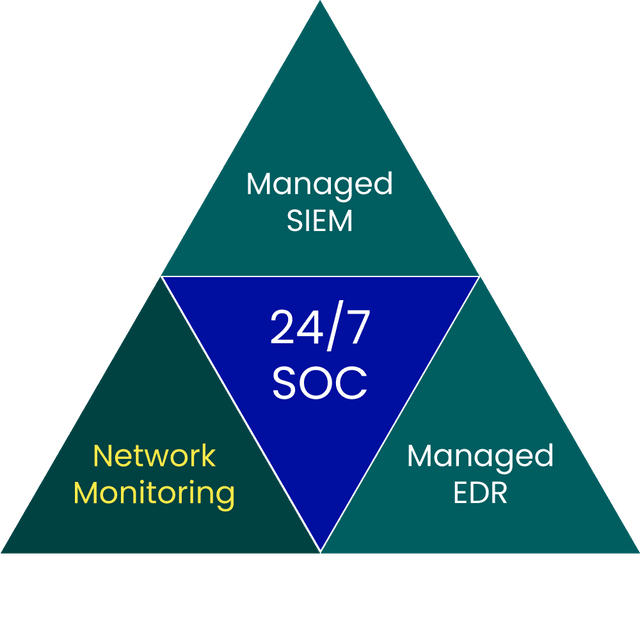
Complete solution
The solution is customised and fully supported by us, so no additional products are required

24/7 network monitoring and analysis by security experts
Network Monitoring
Today, more and more of our business is digital, from the systems we work in, to the production and distribution of what we sell. As a result, we have also become more vulnerable to cyber threats and technical failures, because when IT is at a standstill, everything is at a standstill. Proactively protecting your networks from threats and incidents is therefore essential to ensure the operation of your daily business, as well as compliance with various regulations and customer requirements.
BlueSOC Network Monitoring is our fully managed network monitoring service. The service is staffed by experienced security analysts in our BlueTeam, who monitor your network traffic around the clock to detect malware, unauthorised scanning attempts, policy violations and other intrusion attempts. All alerts are manually validated and enriched, and incidents are reported and escalated to suit your organisation. In this way, our BlueTeam becomes an extension of your internal security team, with the aim of protecting your business from threats and incidents.
Contact uswhy sentor?
the service in brief
Initial design meeting with you, the customer, to identify the location and number of sensors, specific requirements and configuration changes needed
24/7 monitoring activated from Sentor's BlueSOC - service delivery begins
Pre-configured sensors sent to your chosen locations, including instructions for installation and necessary configuration
Continuous updates, adaptations and whitelisting throughout the service period
The sensors are connected by you as a customer, after which we verify communication and monitoring
Monthly reporting and regular service meetings with your assigned Service Delivery Manager
We offer several contact routes and provide feedback as soon as possible. If you have sensitive information, we ask you to use the encrypted method.
+46 8 545 333 00
We answer 24/7
info@sentorsecurity.com
For general inquiries
soc@sentor.se
Use our PGP-key